We’ve previously outlined the importance of having SPF, DKIM and DMARC set up and always functioning across your email domains to maximize email deliverability. (If you haven’t already, check out our full guidance on setting up each of these authentication protocols here)
In our most recent product update, we’re introducing a feature where we’ll check your SPF, DKIM and DMARC protocols are all in place and working automatically every hour (as long as your mailbox is connected to Allegrow).
This means if for any reason your emails start to fail authentication, we’ll be able to detect the issue within 1 hour and reach out to you, making you aware of the issue, so your team can get authentication working again quickly.
TL;DR: SPF, DKIM, and DMARC checks are critical for protecting sender reputation and inbox placement. But even minor DNS changes or forgotten subdomain setups can silently break authentication. Allegrow now runs automatic hourly checks for all three protocols, flagging issues within 60 minutes. This protects domains from silent deliverability risks tied to DNS errors, missing subdomain setups, or sending platform mismatches. With automatic alerts, teams fix problems fast, keeping campaigns visible and domain reputation intact.
How does it work
Simply put, you’ll connect to Allegrow and every hour, we’ll comprehensively test an email you sent to a unique receiver account for SPF, DKIM and DMARC. This means if anything ever does go wrong with your authentication, we’ll let you know about it sooner rather than later.
The only thing you need to make sure of is that your email account is connected to Allegrow and sending emails each day.
This is a built-in alternative to setting up an automated reminder asking you to manually check your authentication protocols every 30-days and every time you create a new domain or subdomain.
What’s the alternative way to check SPF, DKIM, DMARC
There are 2 primary alternatives to checking your authentication protocols manually.
- Check MX by google apps (which is for G Suite users only) will allow you to manually enter your email domain and check if it passes authentication here:
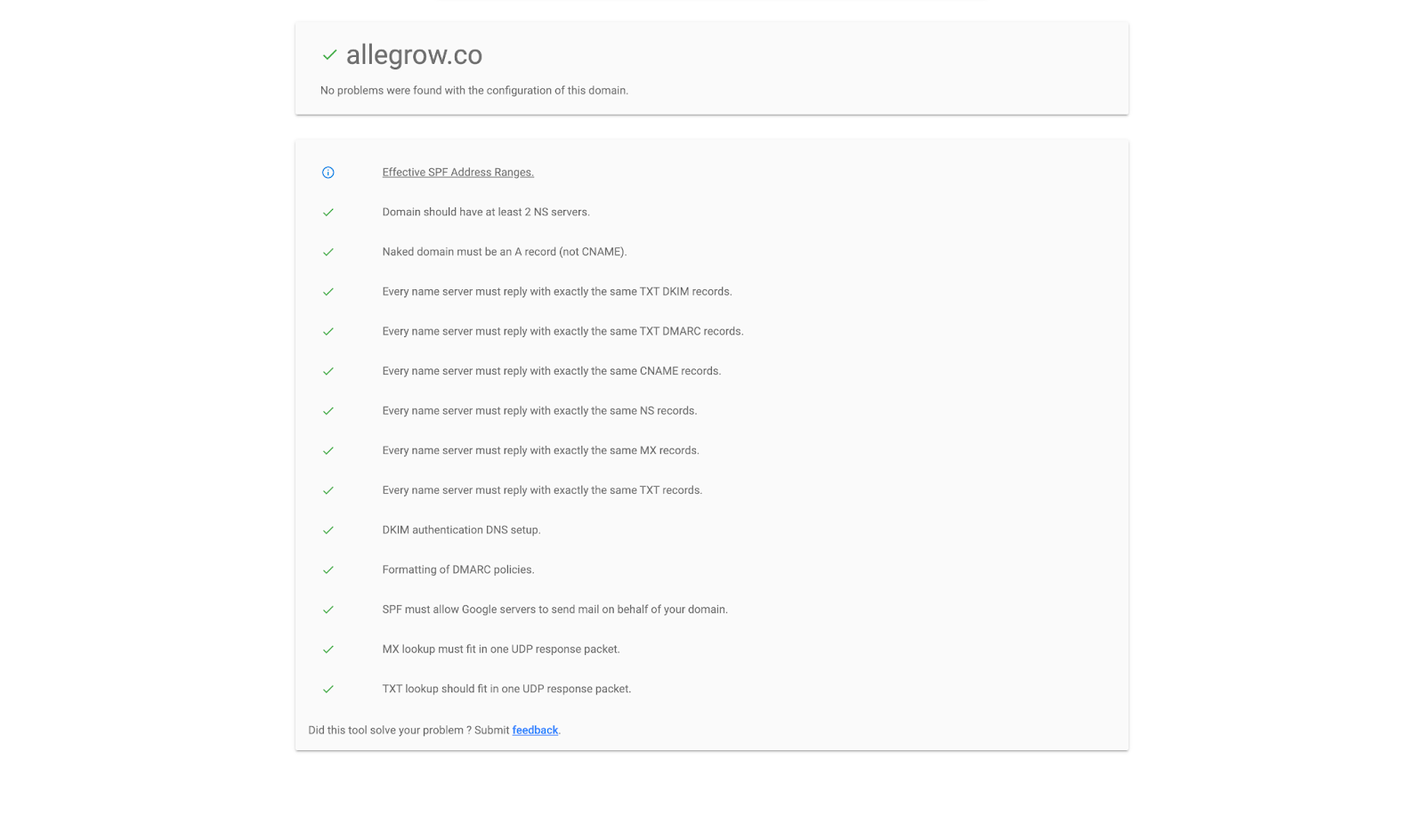
MX checker will also show a pass report like this (which is what you should be aiming for every time you use it)
- Manually checking an email that you sent to an account outside your domain can be examined for authentication without any application if you know what to look for. (example below):
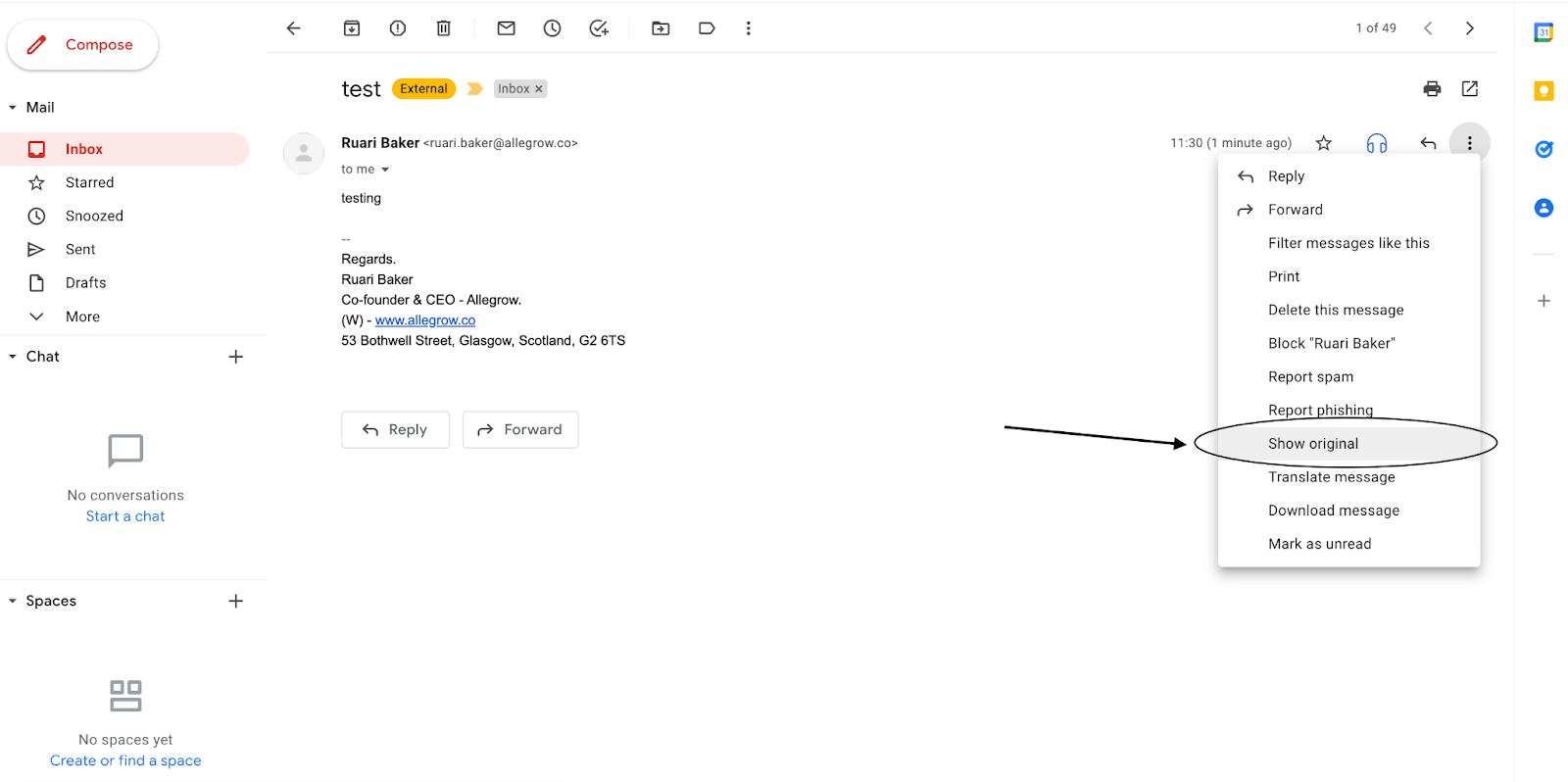
After showing the original message, you can look at the headers, which are automatically summarized in the GSuite interface, to see if there is a ‘PASS’ result for all protocols:

Why is SPF, DKIM and DMARC Important
These three protocols help receiving email accounts verify your identity, clarify that your email has not been tampered with and show that you are being more transparent about your email usage. This essentially means your message is perceived to be less risky and is therefore more likely to land in the primary inbox rather than the spam folder.
As spam accounts form over 41% of global email traffic (Source: Statista), these protocols were created to prevent malicious use of email, such as spoofing. Therefore, having these protocols in place at all times will help you be viewed as a more reputable email sender and improve deliverability.
Why might they stop working?
We’ve seen on multiple occasions businesses who were under the impression DMARC, SPF, and DKIM were all working and in place be surprised when they see emails are failing an authentication check.
Unfortunately, to ensure these protocols are always in place to maximize deliverability requires consistent monitoring. As there are many common reasons that authentication may have stopped working on your domain, such as:
- SPF, DMARC and DKIM were never actually set-up for the specific subdomain or separate domain you're using. As obvious as it sounds, it’s a very common flaw for the protocols to have only been set-up for the main company email domain and none of the other domains which are used for specific purposes (like cold emails or support).
- Your DNS settings/host has changed. If the host of your DNS records changes in any way this may invalidate what you’ve already put in place for authentication.
- The sending mechanism you’re using was never listed on your SPF records correctly. As in order for emails to be fully authenticated if a service or different server is sending emails on your domain, you’ll need to include it on your SPF record.

.jpeg)


.jpg)
